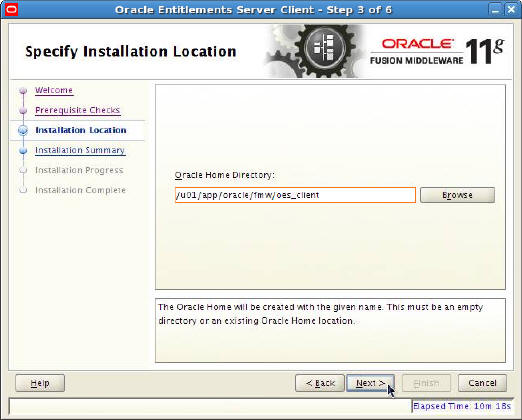
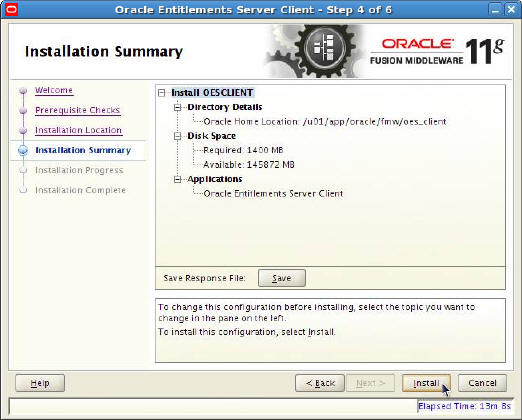
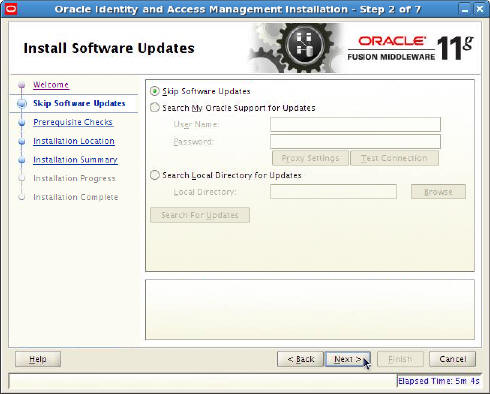
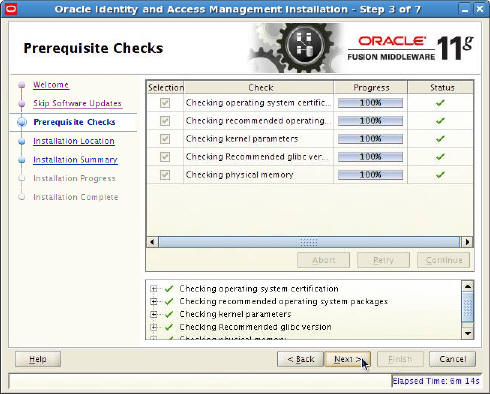
Oracle Service Bus 11g 11.1.1.8 : How to export an OSB project from OSB console and import it in OEPE
1.) On the Right Hand Side pane, select System Administration
2.) Click on Export Resources
3.) Check the project you want to export and click "Export" This will create an export file
4.) Save the .jar file (sbconfig.jar) in a location. We will use this file in OEPE
5.) Assuming if the Eclipse was installed in the folder c:\OSB, please execute C:\OSB\Oracle\Middleware\oepe\eclipse.exe to start eclpipse.
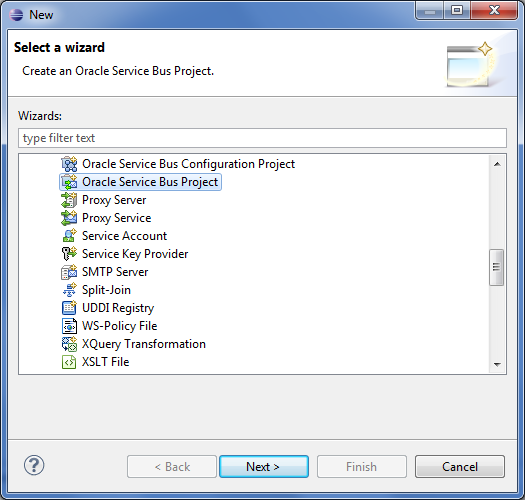
6.) On Eclipse, click on New--> Other--> Oracle Service Bus
7.) Press Next
8.) Put the project name. This may be the same name as the name of the project in OSB console
9.) This will create a project in Eclipse and open Eclipse's OSB perspective.
10.) Right click on Project and import the jar file
11.) Select the jar file that from exported from OSB console
12 .) Select all the check boxes and press Finish
13.) The project is imported. Right click on the Proxy service and Run the service on Server. Please ensure that you have already created the connection using URL:
http://oraclesoaandoim.blogspot.com/2012/04/oracle-service-bus-11115-create-server.html