Oracle API Gateway 11.1.2.3 Virtualizing a Service in API Service Manager
You can use the API Services tab in API Service Manager to virtualize services with the API Gateway. The Business Services repository stores service URLs, definitions and related information such as XML schemas. Clients can query this repository for service information (for example, URLs or WSDL files), and use it to send messages to the service through the API Gateway.
Step 1—Basic Information
The first step in the New API Service wizard enables you to virtualize a service with or without a Web Services Definition Language (WSDL) file.
Virtualizing a REST API-based Service
To virtualize a REST API-based service without a WSDL file, perform the following steps:
Click No, my Service will be defined manually, and enter the details for your service, for example:
Click Next to specify how service is exposed.
Virtualizing a Web Service
To virtualize an example Web service using the API Service Manager, perform the following steps:
Click Yes, I know a URL from which to get a WSDL, and enter a URL in the WSDL URL field, for example:
http://localhost:7070/axis/services/urn:xmltoday-delayed-quotes?wsdl
Click Next to view a WSDL import summary.
Click Next to specify how the service is exposed.
The second step in the wizard enables you to specify how the service is exposed. Perform the following steps:
Enter or select the protocol. Defaults to HTTP. You can also click Show Details to view the default port address (${env.PORT.TRAFFIC} defaults to 8080).
Enter or select the services group. Defaults to Default Services.
Enter the relative path. Defaults to the path after the service domain name (for example, my_service). You may wish to virtualize the service on a different relative path.
Click Next.
Step 3—Request Processing
The third step in the wizard enables you to specify policy packages used for request processing. (for example, an OAuth policy package for authentication. Perform the following steps:
Click the green plus icon, and select a policy package from the list.
Select whether this policy package is Required or Optional. Defaults to Required.
Click the Edit Parameters icon to specify any policy parameters (for example, the value of a message attribute selector such as ${http.request.uri}).
Repeat these steps to add more request processing policy packages.
Click Next when finished.
![[Note]](http://docs.oracle.com/cd/E39820_01/doc.11121/gateway_docs/common_oracle/images/admon/note.png) | Note |
|---|
You can use the Policy Studio to create reusabe policy packages that can be applied to services in API Service Manager.
|
The fourth step in the wizard enables you to specify policy packages used for routing (for example, JMS). Perform the following steps:
Click the green plus icon, and select a policy package from the list.
Select whether this policy package is Required or Optional. Defaults to Required.
Click the Edit Parameters icon to specify any policy parameters (for example, the value of a message attribute selector such as ${http.headers}).
Repeat these steps to add more routing policy packages.
Click Next when finished.
Step 5—Response Processing
The fifth step in the wizard enables you to specify policy packages used for response processing (for example, a policy package that removes sensitive information such as credit card details from the message). Perform the following steps:
Click the green plus icon, and select a policy package from the list.
Select whether this policy package is Required or Optional. Defaults to Required.
Click the Edit Parameters icon to specify any policy parameters (for example, the value of a message attribute selector such as ${content.body}).
Repeat these steps to add more repsonse processing policy packages.
Click Next when finished.
The sixth step in the wizard enables you to select the following monitoring options for the service:
Monitor API Service usage:
Specifies whether to store message metrics for this service. This is selected by default.
Monitor API Service usage per client:
Specifies whether to generate reports monitoring which authenticated clients are calling which services. This is selected by default.
Monitor client usage:
If you want to generate reports on authenticated clients, but are not interested in which services they are calling, select this option and deselectMonitoring service usage per client.
Message Attribute:
Enter the message attribute to use to identify authenticated clients. The default authentication.subject.id attribute stores the identifier of the authenticated user (for example, the username or user's X.509 Distinguished Name).
Click Next when finished.
The final step in the wizard enables you to specify tags for this service. Tags are user-friendly names to help organize, search, and browse API Gateways and services in API Gateway Manager and Policy Studio. Perform the following steps:
Click the green plus icon to add a tag.
Enter a Tag name (for example, Dept).
Enter a Value (for example, QA).
Click Finish.
To view services by tag in API Gateway Manager, perform the following steps:
Click the Show Columns button on the right in the API Services toolbar.
Select the tag that you wish to display.
Click Apply to view tag in the list.
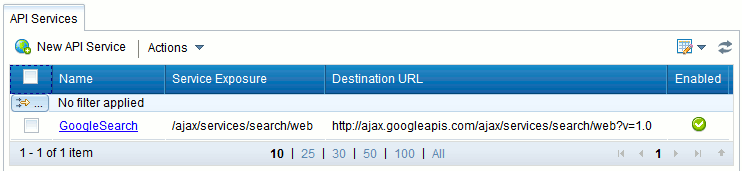
The virtualized service is displayed on the API Services tab:
When you have completed the steps in the wizard, you must deploy the updated configuration to a API Gateway group, or a subset of API Gateways in a group, as follows:
Click Actions -> Deploy on the left in the API Services tab.
In the Deployment Wizard, select the group and API Gateway instance(s) to which you wish to deploy the current working configuration, and click theNext.
Enter a comment for this deployment (for example, registering google search service).
Click Deploy.
Click Finish.
![[Note]](http://docs.oracle.com/cd/E39820_01/doc.11121/gateway_docs/common_oracle/images/admon/note.png)